江民发布“好快”病毒技术分析报告 | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| http://www.sina.com.cn 2005年03月07日 17:09 新浪科技 | ||||||||||
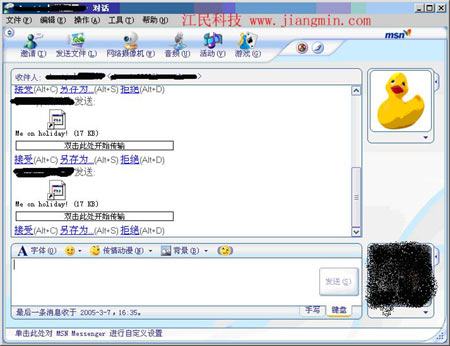 图为MSN“好快”病毒发作时截图 点击此处查看全部科技图片 病毒类型:蠕虫 病毒大小:17429字节 传播方式:网络
危害程度:★★★ 2005年3月7日,江民反病毒中心截获一个通过MSN和P2P软件快速传播的蠕虫病毒I-Worm/MSN.Sofast。 病毒具体技术特征如下: 1. 通过MSN向用户好友发送病毒文件,可能的文件名如下: MSLARISSA.pif CmdPrompt32.pif SP00Lsv32.pif LOVE_LETTER_FOR_YOU.pif WinVBS.vbs MESSAGE_TO_BROPIA.txt Hey LARISSA fuck off, you fucking n00b!.. Bla bla to your fucking Crazy frog gets killed by train!.pif Annoying crazy frog getting killed.pif See my lesbian friends.pif LOL that ur pic!.pif My new photo!.pif Me on holiday!.pif The Cat And The Fan piccy.pif How a Blonde Eats a Banana...pif Mona Lisa Wants Her Smile Back.pif Topless in Mini Skirt! lol.pif Fat Elvis! lol.pif 2. 病毒运行后,将创建下列文件: %SystemDir%\serbw.exe, 17429字节 %SystemDir%\formatsys.exe, 17429字节 %WinDir%\msmbw.exe, 17429字节 c:\crazy-frog.html, 745字节 c:\lspt.exe, 17429字节 c:\crazy frog gets killed by train!.pif, 17429字节 c:\annoying crazy frog getting killed.pif, 17429字节 c:\see my lesbian friends.pif, 17429字节 c:\lol that ur pic!.pif, 17429字节 c:\my new photo!.pif, 17429字节 c:\me on holiday!.pif, 17429字节 c:\the cat and the fan piccy.pif, 17429字节 c:\how a blonde eats a banana...pif, 17429字节 c:\mona lisa wants her smile back.pif, 17429字节 c:\topless in mini skirt! lol.pif, 17429字节 c:\fat elvis! lol.pif, 17429字节 c:\jennifer lopez.scr, 17429字节 c:\message to n00b larissa.txt, 156字节 其中c:\message to n00b larissa.txt内容如下: Hey LARISSA fuck off, you fucking n00b!.. Bla bla to your fucking Saving the world from Bropia, the world n33ds saving from you! '-S-K-Y-'-D-E-V-I-L-' 3. 在注册表中添加下列启动项: [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\Run] "serpe" = %SystemDir%\serbw.exe [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] "serpe" = %SystemDir%\serbw.exe [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices] "serpe" = %SystemDir%\serbw.exe [HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run] "serpe" = %SystemDir%\serbw.exe 这样,在Windows启动时,病毒就可以自动执行。 4. 修改%SystemDir%\drivers\etc\hosts文件,屏蔽多个反病毒网站: 64.233.167.104 www.symantec.com 64.233.167.104 www.sophos.com 64.233.167.104 www.mcafee.com 64.233.167.104 www.viruslist.com 64.233.167.104 www.f-secure.com 64.233.167.104 www.avp.com 64.233.167.104 www.kaspersky.com 64.233.167.104 www.networkassociates.com 64.233.167.104 www.ca.com 64.233.167.104 www.my-etrust.com 64.233.167.104 www.nai.com 64.233.167.104 www.trendmicro.com 64.233.167.104 www.grisoft.com 64.233.167.104 securityresponse.symantec.com 64.233.167.104 symantec.com 64.233.167.104 sophos.com 64.233.167.104 mcafee.com 64.233.167.104 liveupdate.symantecliveupdate.com 64.233.167.104 viruslist.com 64.233.167.104 f-secure.com 64.233.167.104 kaspersky.com 64.233.167.104 kaspersky-labs.com 64.233.167.104 avp.com 64.233.167.104 networkassociates.com 64.233.167.104 ca.com 64.233.167.104 mast.mcafee.com 64.233.167.104 my-etrust.com 64.233.167.104 download.mcafee.com 64.233.167.104 dispatch.mcafee.com 64.233.167.104 secure.nai.com 64.233.167.104 nai.com 64.233.167.104 update.symantec.com 64.233.167.104 updates.symantec.com 64.233.167.104 us.mcafee.com 64.233.167.104 liveupdate.symantec.com 64.233.167.104 customer.symantec.com 64.233.167.104 rads.mcafee.com 64.233.167.104 trendmicro.com 64.233.167.104 grisoft.com 64.233.167.104 sandbox.norman.no 64.233.167.104 www.pandasoftware.com 64.233.167.104 uk.trendmicro-europe.com 5. 结束多种杀毒软件和防火墙进程。 6. 禁止注册表编辑器和任务管理器运行。 7. 通过复制到共享文件夹和P2P软件共享文件夹传播,可能的文件名为Messenger Plus! 3.50.exe 8. 打开网页c:\crazy-frog.html,连接frog.0catch.com/网站。 针对该病毒,江民公司已经在第一时间升级。请广大用户一定要提高警惕,不要点击来自MSN的不明文件,并立即升级到3月7日病毒库,即可全面查杀该病毒,保护您的系统不受威胁。 |
不支持Flash
| 新浪首页 > 科技时代 > 软件 > 行业报告专题 > 正文 |
|
|
|
| |||||||||||||||||||||||||||||||||||||
|
科技时代意见反馈留言板 电话:010-82628888-5595 欢迎批评指正 新浪简介 | About Sina | 广告服务 | 联系我们 | 招聘信息 | 网站律师 | SINA English | 会员注册 | 产品答疑 Copyright © 1996 - 2006 SINA Inc. All Rights Reserved 新浪公司 版权所有 |


